DNS Bind cheat sheet
1 DNS and BIND and named
Domain Name System is the name of the distributed directory database running
across internet name servers that resolve host names to ip addresses.
BIND is the name of the software implementation of this distributed database
implemented on Unix systems. BIND is the Berkley Internet Name Domain s/w.
1.1 bind is the package name, named is the daemon
All references on the system, i.e. starting, stopping, all reference named
and not 'bind'.
2 BIND install
sudo yum list | grep bind # if no yum -y install bind yum -y install bind-utils # or dnf -y install bind dnf -y install bind-utils
dnsutils is not what you are looking for. You are looking for bind-utils
2.1 Sample config files need to be copied into production directories
cp /usr/share/doc/bind/sample/etc/* /etc/ -r cp /usr/share/doc/bind/sample/var/named/* /var/named/ -r
2.2 files
Main configuration file is in /etc/named.conf
this file does not change very much.
2.3 zone files
They are stored in /var/named
These get edited quite often, with errors going to /var/log/messages
unless specified otherwise. In a production environment errors should
got to /var/log/named.log (or something similar)
3 BIND operations.
Starts with queries coming from dns clients.
- name request first looked up in
local cache - on
miss, the dns server looks up theauthoritative NS, ie. who is theSOA. i.e. it sends a dns query forNS recordof thedomainit wants to reach - on reply it again queries this time for
SOA resource record - SOA looks at his
/etc/named.conffiles, in particular thezonedeclarationsto confirm that yes I do have SOA on this domain. - SOA server then follows the
zone declaration pointersto open thezone datafile, eg/var/named/acme.com.zone - if resource found, an
authoritative response is sentto the dnsclient if resource not found, anerroris returned to the dns client.
4 /etc/named.conf typical structure/syntax
<statement-1> ["<statement-1-name>"] [<statement-1-class>] {
<option-1>;
<option-2>;
<option-N>;
};
<statement-2> ["<statement-2-name>"] [<statement-2-class>] {
<option-1>;
<option-2>;
<option-N>;
};
<statement-N> ["<statement-N-name>"] [<statement-N-class>] {
<option-1>;
<option-2>;
<option-N>;
};
- sections are grouped by "stanzas" and delimited by { }
For example, (more detailded than in OPS335 class): // // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. options { listen-on port 53 { 127.0.0.1; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; dump-file "data/cache_dump.db"; same as line above statistics-file "data/named_stats.txt"; memstatistics-file "data/named_mem_stats.txt"; secroots-file "data/named.secroots"; recursing-file "data/named.recursing"; allow-query { localhost; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; /* https://fedoraproject.org/wiki/Changes/CryptoPolicy */ include "/etc/crypto-policies/back-ends/bind.config"; };
5 Recursion vs Iterative DNS queries
5.1 Recursive requests: "buck stops here" (recursion=yes) default is yes.
With these requests your server will attempt to find the website in question
in its local cache. If it cannot find an answer it will query other DNS
servers on your behalf until it finds the address. It will then respond to
the original request with the results from each server's query.
5.2 Iterative requests: "pass the buck" (recursion=no) aka forwarding
With these requests the DNS server will attempt to find the website in
question in its local cache. If it cannot find an answer it will not ask
other DNS servers but will reply back to the original request with a single
“I don't know, but you could try asking this server” message.
By passing the buck you are in less danger of your dns server from being
overwhelmed by "amplifier" attacks. Use recursion=yes with caution.
Home routers typically use forwarding to the ISP DNS server.
5.3 Both occur regularly
Normal internet browsing works with the end client computer by sending its
local configured DNS server a recursive query. That local server then
sends an iterative query to the configured root name servers. What follows
is the usual iterative bunch of queries, all carried out by the local server
to the next tld server, until the local server queries the authoritative
name server that returns the final answer to the local server.
Finally the local server replies to the original recursive query back to the
client that wants to browse it that website.
6 Empty zones
It makes sense for a DNS server NOT to pass queries for RFC1918 addresses
out to the internet root servers, as they will not be able to answer anyway.
Remember that RFC1918 specifies private addreses, 192.168.0.0/16,
172.16.0.0/12 and 10.0.0.0/8 address.
7 Working Examples from my OPS335 class
options {
directory "/var/named";
/* limit who to respond to */
allow-query { 127.0.0.1; 192.168.111.0/24; localhost; };
forwarders { 10.192.100.21; } # for Seneca internal network
/* by using a forwarder, this name server will send unknowns to
this forwarder only, hoping that this name server will have
built up a cache. The request is a recursive one, i.e. let
the forwarder figure out the answer or bust.
if no answer from the forwarder, this name server will contact
the remote servers directly. This query is a non-recursive
query, meaning this server will do the work and get the answer
itself.
*/
# forwarders { 208.67.222.222; 208.67.220.220; } # for home
};
zone "localhost" {
/* master looks up data on local disk specified by the file named */
type master;
/* this contains the database of locally authoritative data */
file "named.localhost";
};
zone "zintis.ops" {
type master;
file "mydb-for-zintis-ops";
};
zone "0.0.127.in-addr.arpa" {
type master;
file "db-127-0-0"; # localhost PTR zone
};
7.1 options section
specify the directory where zone files are stored, usually /var/named
directory "/var/named"; // the default
all references to directories in the options section prepend this directory automatically, so the options config section may look odd for the remaining files
Other options that are not being used in OPS335
options
{
dump-file "data/cache_demp.db";
statistics-file "data/named_stats.txt";
memstatistics-file "data/named_mem_stats.txt";
};
7.2 zone data is in the "view section"
This feature was not availble in bind version 4. bind version 9 though
uses it, and it is the recommended approach. Also, if there is at least
one zone in a "view" section, then ALL zones must be "view" sections.
If named.conf contains no "view" clauses, then all zones are in the default
"view" which matches all clients.
This allows for options to be set for groups of zones, as well as different zones to be served to different types of client addressess.
The followin example has three "views", a local host, internal host view, and and external host view.
view "localhost_resolver" //this sets up named to be a localhost resolver //i.e. caching only nameserver. { /* this view sets up named to be a localhost resolver, and any zone placed in this view will only be seen by the local machine. */ match-clients {localhost; }; match-destinations {localhost; }; recursion yes; # all views must contain the root hints zone: include "/etc/named.root.hints"; include "/etc/named.rfc1912.zones"
7.3 root hints
these are the root "dots" data, and why all FQDN must end in a dot.
8 Origin
With bind, the default origin for the DNS database files is the second field
of the primary or secondary line in the named.boot file.
The origin is the domain name that is appended automatically to all names not
ending in a dot.
If you name server is responsible for multiple domains, you can reset the
origin for various sections of your zone file by using the $ORIGIN field:
$ORIGIN classics.movie.edu. casablanca IN A 10.1.1.5 unforgiven IN A 10.1.1.77 $ORIGIN newest.movie.edu. jojo-rabbit IN A 10.1.1.79 nineteen-seventeen IN A 10.1.1.75
8.1 Origin and SOA resource record:
acme.com. IN SOA coyote.acme.com. admin.coyote.acme.com. ( @ IN SOA coyote.acme.com. admin.coyote.acme.com. (
acme.com.could be shortened to"@"More specifically, the
@gets replaced with the$ORIGIN, and the$ORIGINis deteremined by thesecond field in the named.conf file,right after "zone"For example if the named.conf file has zone "acme.com" then $ORIGIN becomes "acme.com." and @ will be replaced with "acme.com."
- coyote.acme.com. = name of primary (authoritative) name server for acme.com. you could also say coyote.acme.com. if coyote.acme.com. is the authoritative name server for the acme.com. domain
- the root above is the mail address to receive queries about this domain i.e root@acme.com
9 view sections
In /etc/named.conf file, if there is no "view" section, then all the zones
and settings are considered in the 'default' view.
If /etc/named.conf does have a view section, then ALL the zones must be
in view sections.
9.1 Why views?
They allow the DNS server (named) to treat dns queries differently to
different DNS requesters. Typically done to differantiate between inside
dns queries, where you would want to allow all inside hosts to get the
addresses of all other inside hosts, and outside dns queries, where you
might only allows MX records, and your web server records, or maybe
load balancer. Or maybe not allow any queries at all.
So view clauses are like iptable filters. They define match parameters and a subsequent action. The match parameters are defined for a view. Different match parameters are for different views.
Then within each view section, you can configure named to server up the resource records appropriate for that view. (i.e. those clients that matched)
A view clause matches (is invoked) when either or both of its match-clients and match-destinations statements match and when the match-recursive-only condition is met. If either or both of match-clients and match-destinations are missing they default to any (all hosts match).
All zones supported by each view clause must be defined with the view clause allowing a view to respond uniquely for each zone if required.
9.2 view clauses (part of named.conf)
The syntax of a view clause is as follows:
view "view_name" [class] {
[ match-clients { address_match_list } ; ]
[ match-destinations { address_match_list } ; ]
[ match-recursive-only { yes | no } ; ]
// view statements
// zone clauses
};
9.3 view "localhostresolver"
This is for the machine itself. The host that is running named. It is needed for caching-only nameservers, and caching-only nameserver have ONLY this view. entries in this view include: localhost.localdomain 127.0.0.1
9.4 view "internalresolver"
Keep the internal host information secret to the outside wild-west of the internet. It makes it much harder for outside attacks.
view "internal"
{
/*
this view contains zones to serve to internal clients
only that connect via direct attached LAN interfaces
or 'localnets'
*/
match-clients {localnets; };
match-destinations {localhost; };
recursion yes;
// all views must contain the root hints zone:
include "/etc/named.root.hints";
// include "/etc/named.rfc1912.zones" do NOT server
// these to local clients.
// these are the "authoritative internal zones, and would
// probably also be included in the "localhost_resolver"
// view above. That's because it would be odd to resolve
// requests for the rest of your network, or external hosts,
// but not be able to resolve them yourself. therefore
// whatever domains are listed here should also be listed
// in localhost_resolver
zone "my.internal.zone" {
type master;
file "my.internal.zone.db";
};
zone "my.slave.internal.zone" {
type slave;
file "slaves/my.slave.intern
masters { /* put master names here
;
// put slave zones in the slaves/ directory so
//named can update them
};
zone3 "my.ddns.internal.zone" {
type master;
allow-update { key ddns_key; };
file "slaves/my.ddns.internal.zone.db";
// put dynamically updateable zones in the slaves/
key ddns_key
{
algorithm hmac-md5;
secret "use /usr/sbin/dns-keygin to generate TSIG keys";
};
Note that CentOS sets up the dynamic dns keys in the "internal" view
9.5 view "externalresolver"
Host addresess served up here are for outside lookups. Any resource record offered up in responses should be for hardened internet safe servers, or firewalls, or name servers.
view "external"
{
/*
this view contains zones to serve to external clients
that have addresses that are NOT on attached LAN interfaces
or 'localnets'
*/
match-clients {any; };
match-destinations {any; };
recursion no;
// set to no so you do not provide free DNS recursive lookups for
// external clients.
// all views must contain the root hints zone:
include "/etc/named.root.hints";
//These are your "authoritative" external zones and would probably
// contain entries for just your web and mail servers
zone "my.external.zone" {
type master;
file "my.external.zone.db";
};
};
9.6 Example of views used as "split dns" for the SAME domain.
'split' DNS using views
view "trusted" {
match-clients { 192.168.23.0/24; }; // our network
recursion yes;
// other view statements as required
zone "example.com" {
type master;
// private zone file including local hosts
file "internal/master.example.com";
};
// add required zones
};
view "badguys" {
match-clients {"any"; }; // all other hosts
// recursion not supported
recursion no;
// other view statements as required
zone "example.com" {
type master;
// public only hosts
file "external/master.example.com";
};
// add required zones
};
One last succinct example:
view "sitea" {
match-clients {192.168.1.0/24;};
zone "mydomain.com." IN {
type slave;
masters { 192.168.1.100;};
file "sitea_mydomain.com.db";
};
include "/etc/common_zones.conf";
};
view "siteb" {
match-clients {any; };
zone "mydomain.com." IN {
type slave;
masters {192.168.1.100; };
file "mydomain.com.db";
};
include "/etc/common_zones.conf";
};
9.7 views with slave servers
Split zones with tsig keys. Slave servers sometimes get the first zone database from the first view. To enusre each view gets the right database transfered, you can use tsig keys?
view viewa {
allow-transfer { key viewa-tsig; }
...
};
view viewb {
allow-transfer { key viewb-tsig; }
...
};
for the master name server, setting up views is not very complicated. for slave servers though things can get dicey. jensd.be has a good explanation:
9.8 empty zones
For a view that has recursion enabled, default is "empty-zones-enable yes;" Recursion enabled is the "buck stops here" mentality. So if the server will takes on the responsibility of answering the query to the end, it is better to have empty zones available to lookup and respond immediately.
For a view that has recursion disabled, default is "empty-zones-enable no;" Recursion disabled is the "pass the buck" mentality. i.e. let the up-wind server decide to answer with its empty zone, or also pass the buck.
But what are empty zones and why is my dns server creating them? They are automatically configured and loaded (for each view) when named starts. The purpose of these zones is to prevent recursive servers from sending meaningless queries to Internet servers that cannot handle them (thus creating delays and SERVFAIL responses to clients who query for them). These empty zones ensure that immediate and authoritative NXDOMAIN responses are returned instead.
The configuration option empty-zones-enable controls whether or not empty zones are created, whilst the option disable-empty-zone can be used in addition to disable one or more empty zones from the list of default prefixes that would be used.
10 Zones and domains (know the difference)
A zone is a point of delegation in the DNS tree. A zone consists of those contiguous parts of the domain tree for which a name server has complete information and over which it has authority.
It contains all domain names from a certain point downward in the domain tree except those which are delegated to other zones. A delegation point is marked by one or more NS records in the parent zone, which should be matched by equivalent NS records at the root of the delegated zone.
A zone can map exactly to a single domain, but could also include only part of a domain. A good example is the early years of the .ca domain. Ontario and BC were early adopters that ran their own subdomains. so on.ca and bc.ca. They ran their own subdomains and their zones. But the .ca zone included other subdomains in its zone data, like al.ca, mb.ca, ns.ca nl.ca etc. So the zone file had a ragged bottom edge and did not map exactly to a single domain.
10.1 Each zone is served by at least one authoritative name server
This NS contains the complete data for the zone. To make the DNS tolerant of server and network failures, most zones have two or more authoritative servers, on different networks.
11 named.boot file is depracated by named.conf file.
12 Creating a zone 1) /etc/named.conf
The named.conf file has these following commands/sections:
12.0.1 acl
Defines a named IP address match list used for access control. The address match list designates one or more IP addresses (dotted-decimal notation) or IP prefixes (dotted-decimal notation followed with a slash and the number of bits in the netmask). The named IP address match list must be defined by an acl statement before it can be used elsewhere. No forward references are allowed.
12.0.2 include
Inserts an include file at the point where the include statement is encountered. Use include to break up the configuration into more easily managed chunks.
12.0.3 key
Specifies a key ID used for authentication and authorization on a particular name server. See the server statement.
12.0.4 logging
Specifies what information the server logs and the destination of log messages
12.0.5 options
Controls global server configuration options and sets default values for other statements.
12.0.6 server
Sets designated configuration options associated with a remote name server. Selectively applies options on a per-server basis, rather than to all servers.
12.0.7 zone
Defines a zone. Selectively applies options on a per-zone basis, rather than to all zones.
12.1 first you declare the zone, in /etc/named.conf you would have
zone "acme.com" IN { type master; file "acme.com.zone"; allow-update{none; }; };
So acme.com is the domain that needs to be resolved.
There are three types: master these are updated directly. Can be queried slave these are not updated directly, but through zone transfers. Can be queried. hints a very specific thing: "go find me the root servers"
12.1.1 allow-update
specifies who updates this record. (notice the space after none; ) if is {none; }; then only the administrator on this machine can update this zone. i.e. who can add resource records.
if is {192.168.111.1; }; then the dhcp server at .111.1 is allowed to update the zones through dynamic DNS
12.2 where to place the zone
Traditionally can be defined directly in /etc/named.conf The problem is that the zone must be listed in every view that you want the zone to be visible in.
That means if you adminsiter 10 zones, you must list them each at least twice in /etc/named, and make sure that they are both consistent with each other.
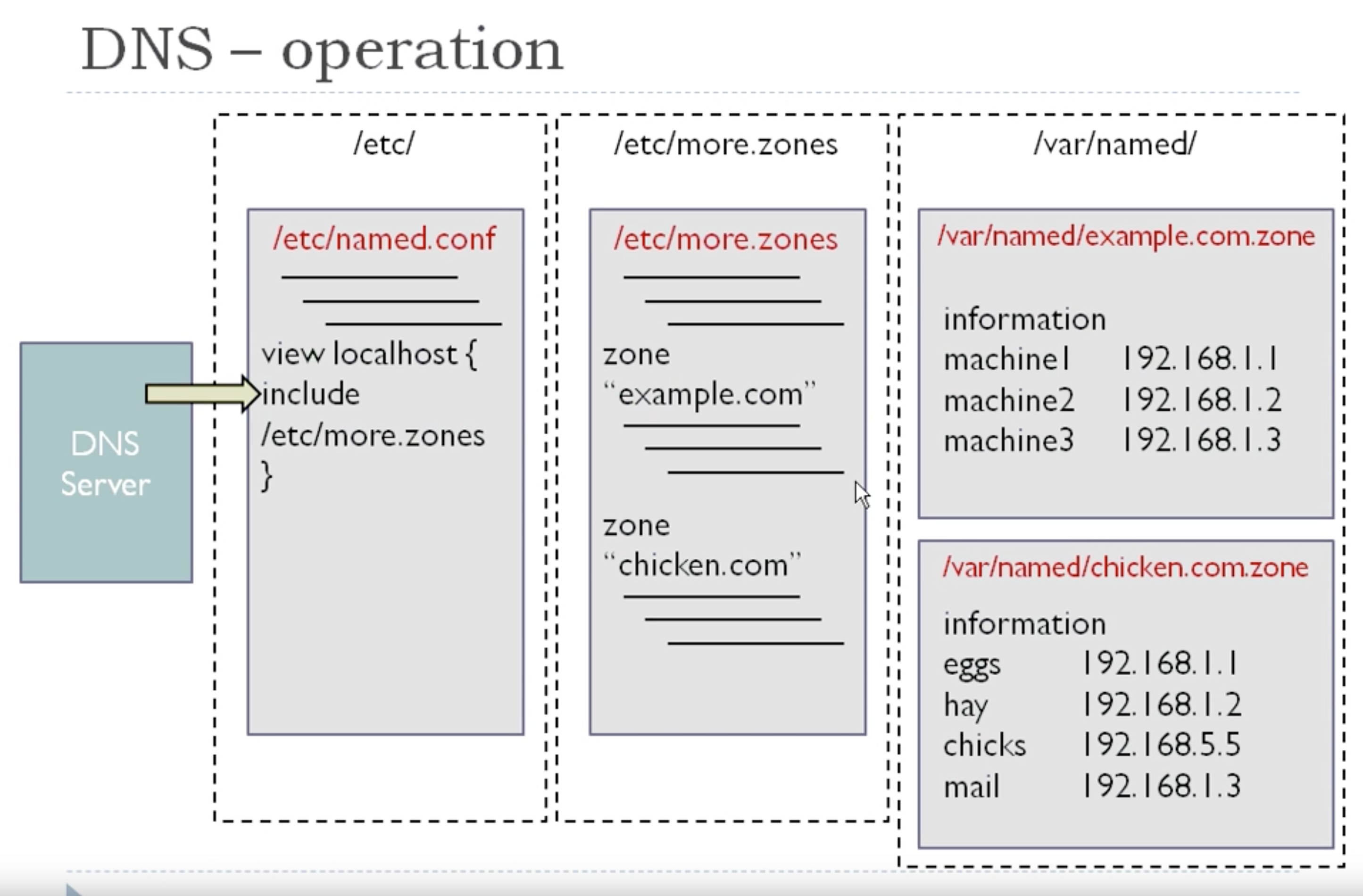
Solution: put the zones that you define yourself into a separate file and use the "include" statement
cat /etc/more.zones
zone "acme.com IN { type master; file "acme.com.zone"; allow-update { none; }; }; zone "dude.com" IN { type master; file "dude.com.zone"; allow-update { none; }; allow-transfer { <ipaddr of slave NS>; }; }; This is a list of additional zones that I administer Then, still in named.conf you can: view "localhosts_resolver" { xxxxxxxx xxxxxxxx include "/etc/named.root.hints"; include "/etc/more.zones"; xxxxxxxx xxxxxxxx }; view "internal" { xxxxxxxx xxxxxxxx include "/etc/named.root.hints"; include "/etc/more.zones"; xxxxxxxx xxxxxxxx }; { };
13 Creating a zone 2) /var/named/localdomain.zone
The actual database, .db files are kept in /var/named for each zone. A good way to start a zone file is copy /var/named/localdomain.zone to the acme.com.zone file and use that as a starting point to edit.
Zone files have to be readable by the named user. Make sure they are not owned by root as named might not be able to read them.
$TTL 86400 is the default time to live. (i.e. 1 day) This tells other name servers how long they should cache the record
acme.com. IN SOA localhost root ( 42 ; serial 3H ; refresh 15M ; retry 1W ; expiry ttl 1D ) ; minimum IN NS localhost MX 10 mail mail IN A 11.1.1.4 nick IN A 42.11.5.213
Notes:
acme.com.could be shortened to"@"but putting the proper fqdn isself-documentingandmy choice.More specifically, the@gets replaced with the$ORIGIN, and the $ORIGIN is deteremined by the second field in thenamed.conffile, right after "zone" For example if thenamed.conffile has zone"acme.com"then$ORIGINbecomes"acme.com."and@will be replaced with"acme.com."localhost= name of the primary name server for acme.com you could also say coyote.acme.com. if coyote.acme.com. is the authoritative name server for the acme.com. domain- the
rootabove is the mail address to receive queries about this domain i.eroot@acme.com - The
serial numberis a way forsecondary NS to keep trackif they need to do azone transfer.for example if a secondary is at 41, it knows that it is one behind so initiates a zone transfer to get current again.
- Recommended SOA Values
example.com. 3600 SOA dns.example.com. hostmaster.example.com. ( 1999022301 ; serial YYYYMMDDnn 86400 ; refresh ( 24 hours) 7200 ; retry ( 2 hours) 3600000 ; expire (1000 hours) 172800 ) ; minimum ( 2 days)Zone files have to be readable by the named user. Make sure they are not owned by root as named might not be able to read them.
$TTL 86400 is the default time to live. (i.e. 1 day) This tells other name servers how long they should cache the record
acme.com. IN SOA localhost root ( 42 ; serial 3H ; refresh 15M ; retry 1W ; expiry ttl 1D ) ; minimum IN NS localhost MX 10 mail mail IN A 11.1.1.4 nick IN A 42.11.5.213
14 Adding a secondary name server
14.1 Edit /etc/named on primary to allow zone tranfers
First, on the primary master server, the zone transfer needs to be allowed. Add the allow-transfer option to the sample Forward and Reverse zone definition in /etc/bind/named.conf.local:
[...]
zone "example.com" {
type master;
file "/etc/bind/db.example.com";
allow-transfer { localhost; ip_secondary; };
};
[...]
zone "1.168.192.in-addr.arpa" {
type master;
notify no;
file "/etc/bind/db.192";
allow-transfer { localhost; ip_secondary; };
};
[...]
Most everthing is the same as the primary, except a few key points.
That means we install and run bind and bind-utils,
We configure /etc/named.conf and /var/named/zonefiles
Actually for localhost and 0.0.127.in-addr.arpa. it is a primary, so you can just copy those sections from /etc/named.conf from the primary.
The zone files for these are also the same, so just copy those too from the primary.
db.cache should also just be copied. So that is three files:
- /etc/named.conf
- /var/named/db-127-0-0
- /var/named/named.localhost # or whatever your implementation calls this.
Now, edit :
14.2 /etc/named.conf (for secondary)
Change every occurance of primary to secondary, except for 0.0.127.in-addr.arpa.
Before the filename on each of these lines, add the ip address of the primary.
14.3 /var/named/zone files
You should only have two zone files in var/named db-local-host and db-127-0-0 You have to add a subdirectory for every primary dns server
14.3.1 var/named
14.4 From bind9.readthedocs.io:
// We are the master server for example.com
zone "example.com" {
type master;
file "example.com.db";
// IP addresses of slave servers allowed to
// transfer example.com
allow-transfer {
192.168.4.14;
192.168.5.53;
};
};
// We are a slave server for eng.example.com
zone "eng.example.com" {
type slave;
file "eng.example.com.bk";
// IP address of eng.example.com master server
masters { 192.168.4.12; };
};
15 Improving DNS security with dnssec
dnssec are security extensions to dns that add digital signatures into DNS so
that DNS queries and responses can be verified using certificates (i.e. public
key cryptography).
The queries and responses (recursive) from dns clients are not actually
encrypted. What is added are the steps taken in iterative queries between the
recursive dns servers and the root, tld, and authoritative dns servers. Even
that is not encrypted, but the data exchanged is signed using public key
cryptography, so that the data received can be verified as not being poisoned,
but legit.
15.1 dnssec adds these resource record types:
RRSIGdigital resource record signatureDNSKEYpublic keyDSparent-childNSECproof of non-existenceNSEC3proof of non-existenceNSEC3PARAMproof of non-existenceCDSchild-parent signallingCDNSKEYchild-parent signalling
The details can be read from the docs at this link: bind9.readthedocs.io
15.2 Iterative dns queries
Reminding you that a local server will receive a recursive dns query from its
clients, then repeatedly issue iterative dns queries to root, tld and
authoritative dns servers. The recursive server handles all subsequent queries
until the authoritative answer is found. The recursive server is also known as
validating resolver
Each iterative query is signed using the private key of the sending server and
is checked using its public key by the receiver.
These DNS responses signatures are sent using the RRSIG resource record.
The signatures are created in the following way.
- Every dns record of message has a hash function applied to get a hash value for the message.
- This hash is then encrypted using the server's private key.
- The encrypted hash is the signature.
Checking validity occurs as follows:
- the message is run through the same hash function by the receiver and the new hash is recorded.
- the accompanying signature is decrypted using the public key of the sending server.
- the resulting decrypted hash (signature) is compared to the hash of the computed by the receiver. The hash should match if data has not changed, (integrity intact) and the sender validated (authenticity validated).
15.3 Zone transfers
Here too the servers involved will sign the data about to be transmitted by the primary dns server for the zone data, before the transfer happens. Then the secondary dns server will confirm that the signature checks out using the primary servers public key.
The public keys are published as part of the zone data and stored in the
DNSKEY resource records. The DNSKEY records store the keys. There are the
Zone Signing Keys, ZSK, used to protect the zone data, and Key Signing Keys
used to sign the zone's keys. If the same key is used for both roles that
key is called a Combined Signing Key, CSK.
For the parent-child relationship (primary-secondary dns servers) there are
several other records used between them. The DS, CDS, and CDSKEY records.
They all use public-private key cryptography to sign and verify signatures
between server that do zone transfers.
15.4 Proof of non-existence
Spoofed DNS servers could attempt to add bogus DNS responses to queries. So
it is important to not just say this data is correct, but also to say, that
data does not exist. The resource records NSEC, NSEC3, and NSEC3PARAM records
are created for these reasons.
16 Troubleshooting named configuration
Couple of reminder notes:
- named is controlled by
systemctl - named reads
/etc/named.confon starting - zone files usually in
/var/namedand or/var/named/slavesbut can be over-ridden by directory statement in /etc/named.conf - ss status (sudo systemctl status) named will tell you if you have errors.
- if you do have errors on starting (or restarting) then loop at either:
a)
/var/log/messagesb) sss (sudo systemctl status) named - The messages there will point to what was causing the error. Fix it and restart at 4)
I used alias sss='sudo systemctl status' Also visudo then increase the sudo default timeout by changing the line: envreset to envreset, timestamptimeout=30
16.1 named-checkzone
named-checkzone -i full 105.28.172.in-addr.arpa /var/named/slaves/mydb-for-172-28-105
named-checkzone 105.28.172.in-addr.arpa /var/named/slaves/mydb-for-172-28-105
17 Checking tools
17.1 Checking config
/etc/init.d/named configtest
17.2 Checking named.conf
named-checkconf named-checkconf /etc/named.conf
17.3 Checking
named-checkzone ZONENAME FILE named-checkzone continents.earth.ops /var/named/continents.example.com named-checkzone 10.in-addr.arpa /var/named/named.rev
17.4 Update Zone configs
All zone contents: rndc reload
Update earth.ops zone contents rndc reload earth.ops
Add new zone file: rdnc reconfig
[user01@centos7 ~]$ while : ; do echo -n "`date ` : " ; dig google.com | grep ^google.com ; sleep 1 ; done Wed May 24 20:12:16 JST 2017 : google.com. 164 IN A 172.217.26.46 Wed May 24 20:12:17 JST 2017 : google.com. 163 IN A 172.217.26.46 Wed May 24 20:12:18 JST 2017 : google.com. 161 IN A 172.217.26.46 Wed May 24 20:12:19 JST 2017 : google.com. 160 IN A 172.217.26.46 Wed May 24 20:12:20 JST 2017 : google.com. 159 IN A 172.217.26.46 Wed May 24 20:12:21 JST 2017 : google.com.
18 DNS clients
18.1 dig
Use dig @server lookupthishost
dig -x 172.28.105.100dig vm1.zintis.opsdig vm2.zintis.opsdig -x +noall +answer 172.28.105.101
18.2 dig +trace
for following through non-recursive lookups for each stage (You will see the response from the root servers, . , the .com. servers, and cisco.com. servers. )
- check the fireall (iptables) rules. My VMs did not allow this (host was fine)
18.3 host
But if you are solely looking for the A record, it is simpler to use:
host vm1.zintis.opshost vm2.zintis.ops antarcticahost vm3.zintis.ops c8host vm4.zintis.ops aushost c8host.zintis.opshost google.com aushost 139.177.192.45host vm1host vm2host vm3host vm4host c8hosthost google.com
man host to see other options, including PTR resource records, and SOA records
eg host -t soa zintsi.ops or also, host -t PTR 192.168.111.5
18.4 host to do a manual zone transfer:
host -t axfr continents.earth.ops or host -t axfr continents.earth.ops australinea
18.5 nslookup
oldest of the three but improved over the years. See man pages for details, or just try nslookup -t SOA continents.earth.ops or just nslookup vm3
nslookup -querytype=SOA zintis.opsnslookup -querytype=PTR 192.168.111.11nslookup vm1.zintis.opsnslookup vm1.zintis.ops australilneanslookup vm1.zintis.ops australilnea.continents.earth.opsnslookup vm2.zinti.ops c8nslookup eu c8nslookup eu ausnslookup eu ant
19 Conflicting info online for Redhat (dated Jan 2020)
You can edit a text file. Find out and set up the value for HOSTNAME in the file /etc/sysconfig/network:
Setup/replace HOSTNAME HOSTNAME=web.nixcraft.com
Where, web is hostname and nixcraft.com is your DNS domain name.
Because apparently using hostnamectl will work but it is transient. WIll have to check that… Feb 20, 2020
20 RNDC (Remote Name Daemon Control)
RNDC is a name server control utility in bind. This name server control utility allows command line administration of the named service both locally and remotely. It is a command line utility and it controls the operation of a name server.
20.1 RNDC files
in /etc/rndc.conf
20.2 RNDC info online
I took the following right out of interserver.net
If the rndc configuration file /etc/rndc.conf does not exist, the utility will use the key located in /etc/rndc.key, which was generated automatically during the installation process using the rndc-confgen -a command. Rndc configuration file specifies which server controls and what algorithm the server should use. To prevent unauthorized users to the named daemon, BIND uses a shared secret key authentication method to grant privileges to particular hosts. It means that an identical key must be present in the configuration file of bind, /etc/named.conf and configuration file, /etc/rndc.conf.
Rndc uses a TCP connection to communicate with the name server. It sends commands authenticated with digital signatures over a TCP connection. HMAC-MD5 is the authentication algorithm supported in the current versions of rndc and named. This uses a shared secret on each end of the TCP connection. This provides a TSIG-style authentication for the command request and the name servers response.
The rndc configuration file consists of three statements:
- Option statement
- Server Statement
- Key statement
The option statement consists of three clauses default-server clause, default-key clause and default-port clause. The default-server clause is followed by the name or address of the name server. This host is used when a no name server is given as an rndc argument. The default-key clause is followed by the name of a key which is identified by a key statement. This default key will be used for authenticating a server when there is no key clause found in a matching server statement, and no keyid is provided in the rndc command line. The default port clause is followed by the port to connect to the remote name server. This default port will be used when no port option is provided on the rndc command line and no port clause is found in a matching server environment.
The server statement includes two clauses, the key and port. The key name must match the name of a key statement in the file. The server statement consists of a string which is the name server address or the host name of name server.
The key statement starts with the name of the key. It consists of two clauses algorithm and a secret clause. Algorithm identifies the encryption algorithm for rndc, currently HMAC-MD5 is used. Secret clause contains the base-64 encoding of the algorithm encryption key.
Rndc reads a configuration file to determine how to contact the name server and decide what algorithm and key it should use.
syntax of rndc takes the following form: –
rndc [option…] command [command-option]
If rndc is invoked with no command-options or arguments, it prints a short summary of the supported commands and the available options and arguments. To display options of rndc command use #rndc
Commands used in rndc are: –
.halt -It is used to stop the named service.
.querylog -logs all queries made to the name server.
.refresh -used to refreshes name server database.
.reload -reloades the zone file.
.stats -dumps the current named stats to the /var/named/named.stats file
.stop -stops the server gracefully.
Options of rndc includes: –
-c <configuration file> -specifies the alternate location of a configuration file.
-p <port number> -Specifies a port number to use rndc other than port 953.
-s <server> -specifies a server other than default- server listed in /etc/rndc.conf file.
-y <key name> -specifies a key other than default-key option in the /etc/rndc.conf file.
To reload the server, use command
#rndc reload
Limitations of rndc: –
- rndc does not yet support all the commands of the BIND 8 ndc utility.
- There is currently no way to provide the shared secret for a keyid without using the configuration file.
- Several error messages could be clearer.
21 Example localhost domains, forward and reverse
21.1 First in /etc/named.conf
zone "zintis.ops" { type master; file "mydb-for-zintis-ops"; allow-query { any; }; allow-update { none; }; }; zone "localhost" { type master; file "named.localhost"; };
21.2 Then mydb-for-zintis-ops zone file
$TTL 3H ;; Don't forget the three trailing dots in the next line. @ IN SOA c8host.zintis.ops. hostmaster.zintis.ops.( 7777 ; serial 8H ; refresh 2H ; retry 1W ; expire 1D ; negative cache TTL ); IN NS c8host.zintis.ops. ; remember trailing dot ; ; Host addresses ; localhost IN A 127.0.0.1 AAAA ::1 c8host IN A 172.28.105.1 IN A 192.168.111.1 IN A 192.168.2.19 host111 IN A 192.168.111.1 host105 IN A 172.28.105.1 hostext IN A 192.168.2.19 c8 IN CNAME c8host vm1 IN A 192.168.111.11 vm2 IN A 192.168.111.12 vm3 IN A 192.168.111.13 vm4 IN A 192.168.111.14
22 Good example
In /etc/named.conf:
listen-on port 53 { 192.168.0.2; };
In both forward and reverse zone files, code:
@ IN SOA FQDN. DOMAIN-NAME. (;don't forget the trailing dot in two places@ IN SOA FQDN. DOMAIN-NAME. (@ IN SOA FQDN. DOMAIN-NAME. (
In forward zone file, code:
IN NS FQDN. ; don't forget the trailing dot
IN A 192.168.0.2
server-name IN A 192.168.0.2
reverse zone file code:
IN NS FQDN. ; dont' forget the trailing dot
2 IN PTR server-name
FQDN = full name of server i.e server1.acme.com. This assumes your server ip is 192.168.0.2
23 Good example of named.conf using view
options {
listen-on port 53 { 127.0.0.1; 10.0.3.56; };
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
query-source port 53;
// query-source-v6 port 53;
allow-query { localhost; 10.0.0.0/20; };
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
view localhost_resolver {
match-clients { localhost; 10.0.0.0/20; };
match-destinations { localhost; 10.0.0.0/20; };
recursion yes;
include "/etc/named.rfc1912.zones";
zone "example.com" IN {
type master;
file "example.zone";
allow-update { none; };
};
zone "3.0.10.in-addr.arpa" IN {
type master;
file "example.local";
allow-update { none; };
};
};
24 Example on $ORIGIN
http://www.zytrax.com/books/dns/ch8/origin.html
$ORIGIN defines a base name from which 'unqualified' names (those without a terminating dot) substitutions are made when processing the zone file.
When set to only a dot . that means that only a dot is going to be added/substituted. That’s all.
Typically you would see:
$ORIGIN example.com. @ IN NS ns1.example.com @ IN NS ns2.example.com. @ IN MX 5 mail
Which because the @ symbol is a shorthand for the $ORIGIN in zone files will be completed into:
example.com. IN NS ns1.example.com.example.com. example.com. IN NS ns2.example.com. example.com. IN MX 5 mail.example.com.
Where the first line shows a typical erroneous record that will result of such substitution when the $ORIGIN gets appended to what was intended to be a FQDN which lacked the trailing . .
Setting $ORIGIN to a dot makes the use of the @ shorthand impractical but will prevent mishaps such as the top one.
$ORIGIN . example.com IN NS ns1.example.com. example.com. IN NS ns2.example.com
Will autocomplete/correct that into
example.com. IN NS ns1.example.com. example.com. IN NS ns2.example.com.
And not into
example.com.example.com. IN NS ns1.example.com. example.com. IN NS ns2.example.com.example.com.
which is what would have happened if the $ORIGIN would still have been the example.com. domain.
25 Notes on local caching server…
If your DNS server is a local caching server, set
allow-query { <your subnet>; }; in options. And, in each zone:
allow-query { any; }; If you are not using it as a caching server, set it on options to none;
allow-query { none; }; Basically, you don't want your server answering to domains you are not authoritative.
26 root servers
They are maintained by IANA and INTERNIC.
You can ftp or http them from http://www.internic.net/domain/named.root
You get this:
; This file holds the information on root name servers needed to ; initialize cache of Internet domain name servers ; (e.g. reference this file in the "cache . <file>" ; configuration file of BIND domain name servers). ; ; This file is made available by InterNIC ; under anonymous FTP as ; file /domain/named.cache ; on server FTP.INTERNIC.NET ; -OR- RS.INTERNIC.NET ; ; last update: April 29, 2020 ; related version of root zone: 2020042901 ; ; FORMERLY NS.INTERNIC.NET ; . 3600000 NS A.ROOT-SERVERS.NET. A.ROOT-SERVERS.NET. 3600000 A 198.41.0.4 A.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:ba3e::2:30 ; ; FORMERLY NS1.ISI.EDU ; . 3600000 NS B.ROOT-SERVERS.NET. B.ROOT-SERVERS.NET. 3600000 A 199.9.14.201 B.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:200::b ; ; FORMERLY C.PSI.NET ; . 3600000 NS C.ROOT-SERVERS.NET. C.ROOT-SERVERS.NET. 3600000 A 192.33.4.12 C.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2::c ; ; FORMERLY TERP.UMD.EDU ; . 3600000 NS D.ROOT-SERVERS.NET. D.ROOT-SERVERS.NET. 3600000 A 199.7.91.13 D.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2d::d ; ; FORMERLY NS.NASA.GOV ; . 3600000 NS E.ROOT-SERVERS.NET. E.ROOT-SERVERS.NET. 3600000 A 192.203.230.10 E.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:a8::e ; ; FORMERLY NS.ISC.ORG ; . 3600000 NS F.ROOT-SERVERS.NET. F.ROOT-SERVERS.NET. 3600000 A 192.5.5.241 F.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2f::f ; ; FORMERLY NS.NIC.DDN.MIL ; . 3600000 NS G.ROOT-SERVERS.NET. G.ROOT-SERVERS.NET. 3600000 A 192.112.36.4 G.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:12::d0d ; ; FORMERLY AOS.ARL.ARMY.MIL ; . 3600000 NS H.ROOT-SERVERS.NET. H.ROOT-SERVERS.NET. 3600000 A 198.97.190.53 H.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:1::53 ; ; FORMERLY NIC.NORDU.NET ; . 3600000 NS I.ROOT-SERVERS.NET. I.ROOT-SERVERS.NET. 3600000 A 192.36.148.17 I.ROOT-SERVERS.NET. 3600000 AAAA 2001:7fe::53 ; ; OPERATED BY VERISIGN, INC. ; . 3600000 NS J.ROOT-SERVERS.NET. J.ROOT-SERVERS.NET. 3600000 A 192.58.128.30 J.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:c27::2:30 ; ; OPERATED BY RIPE NCC ; . 3600000 NS K.ROOT-SERVERS.NET. K.ROOT-SERVERS.NET. 3600000 A 193.0.14.129 K.ROOT-SERVERS.NET. 3600000 AAAA 2001:7fd::1 ; ; OPERATED BY ICANN ; . 3600000 NS L.ROOT-SERVERS.NET. L.ROOT-SERVERS.NET. 3600000 A 199.7.83.42 L.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:9f::42 ; ; OPERATED BY WIDE ; . 3600000 NS M.ROOT-SERVERS.NET. M.ROOT-SERVERS.NET. 3600000 A 202.12.27.33 M.ROOT-SERVERS.NET. 3600000 AAAA 2001:dc3::35 ; End of file